Introduction:
In a startling revelation that underscores teh ongoing threat of cybercrime, security analysts have identified a sophisticated wave of attacks targeting six prominent South Korean firms, attributed to the Lazarus Group, a notorious hacking collective linked to North Korea. Utilizing a combination of vulnerabilities in Cross EX and Innorix platforms, along with the deployment of the elusive ThreatNeedle malware, these cyber intrusions represent a significant escalation in tactics that have raised alarm bells across the cybersecurity community.As organizations grapple with the implications of these breaches, experts warn that the incident highlights not only the vulnerabilities within corporate infrastructures but also the persistent menace posed by state-sponsored cyber actors. This article delves into the specifics of the attack, the methods employed, and the broader implications for South Korea’s cybersecurity landscape.
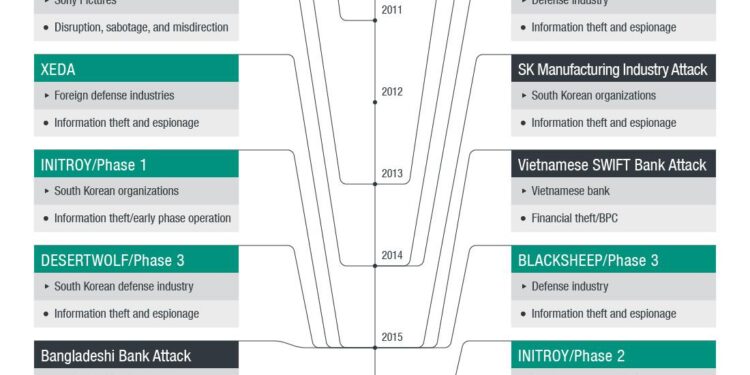
Lazarus Group’s Targeted Assault on South korean Firms Exposed
The notorious Lazarus Group has launched a sophisticated cyberattack targeting six prominent South Korean firms, leveraging vulnerabilities in Cross EX and Innorix alongside the deployment of a potent new strain of malware known as ThreatNeedle. This coordinated assault highlights the group’s capability to exploit existing security weaknesses, posing a substantial risk to companies engaged in sectors critical to the national economy. Among the attacked firms, many are involved in technology and defense, indicating a more extensive strategy to undermine essential infrastructures.
According to cybersecurity experts, the prosperous breaches were made possible due to the companies’ unpatched software and insufficient security measures. The attack has not only disrupted operations but also compromised sensitive data,possibly impacting thousands of stakeholders.In response, affected organizations are urged to prioritize immediate security audits and enhance their defense mechanisms. The incident is a stark reminder of the evolving threat landscape, necessitating a proactive approach to mitigate the risks posed by such advanced persistent threats.
| Firm Name | Sector | Exploited Vulnerability |
|---|---|---|
| Company A | Technology | Cross EX |
| Company B | Defense | Innorix |
| Company C | Finance | Cross EX |
| Company D | Telecommunications | Innorix |
| Company E | Manufacturing | Cross EX |
| Company F | Health | Innorix |
Analyzing the Cross EX and Innorix Vulnerabilities Behind the Attacks
The recent wave of attacks attributed to the Lazarus group has underscored the critical vulnerabilities present in both the Cross EX and Innorix platforms. These exploits allowed attackers to breach security perimeters, afterward compromising sensitive information across multiple South Korean firms. The vulnerabilities within Cross EX are primarily linked to inadequate input validation and a lack of robust authentication mechanisms,which enabled unauthorized access to critical systems. Similarly, the Innorix flaws have been traced back to outdated software components and weak patch management policies, creating easy entry points for malicious actors to deploy their payloads.
Security experts have cautioned against the use of legacy systems that are no longer supported or frequently updated, as seen with these two platforms. A combination of these factors led to the deployment of ThreatNeedle malware,which has been notorious for its stealthy infiltration and data exfiltration capabilities. Organizations are advised to consider a multi-layered security approach, emphasizing the importance of:
- Regular Security Audits: To identify and remediate vulnerabilities in real time.
- Timely Patch Management: ensuring the latest security updates are applied across all software.
- Employee Training: Enhancing awareness regarding social engineering tactics commonly employed in such attacks.
| Vulnerability Name | Impact | Recommendation |
|---|---|---|
| Cross EX Authentication Flaw | Unauthorized Access | Implement Two-Factor Authentication |
| Innorix software Vulnerabilities | Data Exfiltration | Regularly Update Software Components |
strategic Recommendations for Enhancing Cybersecurity Against Lazarus Threats
To bolster defenses against the increasingly sophisticated tactics employed by Lazarus Group, organizations should prioritize an integrated approach to cybersecurity that includes proactive measures and employee training. Key strategies involve:
- Conducting regular vulnerability assessments to identify and patch weaknesses in software,notably in widely used platforms like Cross EX and Innorix.
- Implementing complete threat intelligence solutions that provide real-time alerts on emerging malware threats, including ThreatNeedle.
- Establishing a robust incident response plan to ensure swift action in the event of a breach, minimizing potential damage.
- Engaging in regular training sessions for employees to improve awareness regarding phishing schemes and social engineering tactics.
Furthermore, fostering a culture of cybersecurity within the organization can considerably reduce risks. One effective method is the deployment of a security operations center (SOC) equipped with advanced SIEM (Security Information and Event Management) capabilities. This center can facilitate the monitoring of network traffic and user behavior, enabling early detection of anomalies. The following table outlines critical elements to consider when enhancing cybersecurity posture:
| Element | Description | Importance |
|---|---|---|
| Employee Training | Regular sessions to educate staff on cybersecurity risks. | High |
| Patching Protocols | Systematic updates to fix known vulnerabilities. | Critical |
| Threat Intelligence | Tools for real-time updates on threats. | Essential |
| Incident Response | Preparedness for immediate action during a breach. | Vital |
Insights and Conclusions
the recent cyberattacks attributed to the Lazarus Group targeting six South Korean firms highlight the ongoing threat posed by sophisticated malware and vulnerabilities within the digital landscape. The exploitation of Cross EX, alongside the weaknesses in Innorix, underscores the urgent need for heightened cybersecurity measures across industries.As organizations grapple with the implications of ThreatNeedle malware, the necessity for robust defense mechanisms and proactive threat intelligence becomes increasingly evident. This incident serves as a stark reminder of the ever-evolving tactics employed by cybercriminals and the critical importance of vigilance in safeguarding sensitive data. Stakeholders must remain alert and prepared in the face of these persistent threats that not only disrupt operations but also jeopardize the integrity of national security and economic stability.


![[Minute to Read] Exclusive: Seoul falsified DMZ report to protect peace pact – 조선일보](https://asia-news.biz/wp-content/uploads/2025/04/157179-minute-to-read-exclusive-seoul-falsified-dmz-report-to-protect-peace-pact-eca1b0ec84a0ec9dbcebb3b4-350x250.jpg)













